Subscribe to our newsletter!
Stay updated with the latest security news, tips, and promotions.
 And we made it again! ZoneAlarm Anti-Ransomware was rated “Editors’ Choice” and referred to as “a clear winner” for the second year in a row by PC Magazine. Based on the same technology that powers Check Point’s enterprise-grade product SandBlast Anti-Ransomware, Zone Alarm Anti-Ransomware went up against several competing products in a comprehensive review of the marketplace.
And we made it again! ZoneAlarm Anti-Ransomware was rated “Editors’ Choice” and referred to as “a clear winner” for the second year in a row by PC Magazine. Based on the same technology that powers Check Point’s enterprise-grade product SandBlast Anti-Ransomware, Zone Alarm Anti-Ransomware went up against several competing products in a comprehensive review of the marketplace.
“Check Point ZoneAlarm Anti-Ransomware is one of the most effective ransomware-specific security tools we’ve seen. In testing, it showed complete success against all our real-world samples,” read the PCMag article published on June 21, 2018. “It successfully protected against real-world ransomware samples and cleaned up all traces of ransomware in testing. Very easy to use.”
It was the second time PCMag’s lead analyst for security Neil J. Rubenking rated ZoneAlarm Anti-Ransomware. The first evaluation was performed on Aug. 22, 2017, when the solution was initially awarded the precious Editors’ Choice red stamp.
“We’re really proud of this important achievement. PCMag is one of the most influential and reliable sources in the tech world,” said Dror Levy, head of consumer marketing, ZoneAlarm. “ZoneAlarm Anti-Ransomware uses the most advanced technology against cyber blackmail targeting home users as well as small businesses.”
As PCMag notes, ZoneAlarm not only detects and blocks ransomware – it also restores any damage caused by the attack. Fully compatible with all antivirus solutions, ZoneAlarm Anti-Ransomware offers the best-in-class cybersecurity firepower that the world’s largest banks, governments and organizations rely on.
The ransomware protection you’ve been looking for
Ransomware, when hackers hijack your PC and hold your data hostage until you pay a ransom, is the world’s No.1 cyber security threat and remains the big malware baddie in 2018. Last year, ransomware cost victims approximately $5 billion and there was a 90 percent increase in the number of detected attacks in comparison to 2016. The global ransomware damage costs predicted may hit $11.5 billion by 2019. ZoneAlarm Anti-Ransomware has proved to have the best results against known and never-seen-before attacks.
Cutting-edge technology is obviously a must in order to combat modern sophisticated ransomware. ZoneAlarm Anti-Ransomware keeps you one step ahead of cyber blackmail attacks today, and defends you against new variants that may appear in the future.
Simple and user-friendly anti-ransomware
Every 10 seconds someone gets hit by ransomware. The malware hits without discrimination or notice, penetrating through web, email or removable media devices. ZoneAlarm Anti-Ransomware preserves your life’s most precious memories stored there, including photos, documents, and other personal files that matter only to you, keeping ransom seekers away.
Anti-ransomware isn’t known for its simplicity – and that’s a barrier to protection, as user error is a major factor in successful breaches. ZoneAlarm, with its intuitive and simple user interface, seeks to minimize user error as a way to maximize its effectiveness. PCMag noted this ease-of-use, writing positively about the lack of clutter in the main screen.
How ZoneAlarm Anti-Ransomware works
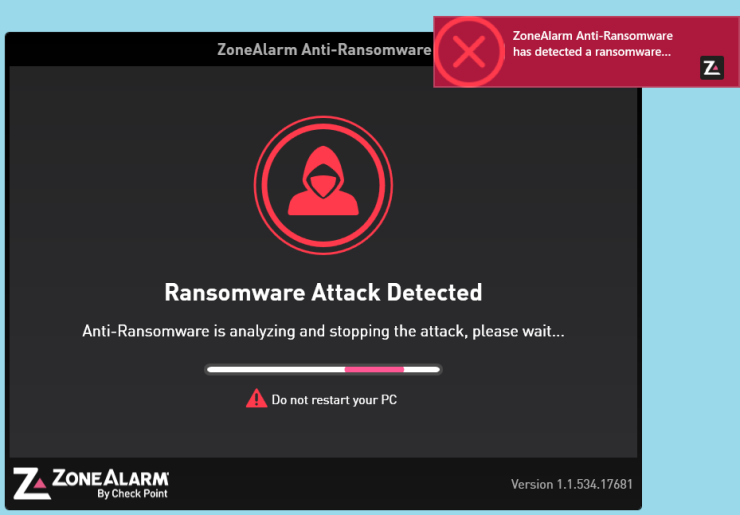
ZoneAlarm Anti-Ransomware utilizes advanced security engines and algorithms to detect, block and remediate ransomware attacks. By using behavioral technologies which do not rely on signature updates, it is able to identify and remediate zero-day ransomware attacks.
ZoneAlarm Anti-Ransomware utilizes a multilayered security architecture, providing a complete solution:
Click here to learn more and buy now our award-winning protection against ransomware attacks. If you prefer, enjoy our 30-day free trial and let us work for you!
Get peace of mind about your PC security. Ransom-proof your digital life with ZoneAlarm.
Research and Resources
Defend yourself with more information using the resource links below.